If you’re looking to gain control over who can access your AWS resources, you’ll want to know about AWS Identity and Access Management (IAM) policies. These policies are designed to help you define permissions in a structured way, with all the key elements you need to ensure your security is top-notch.
Version
When crafting a policy, it’s important to specify the policy version. This field is required and actually helps AWS better understand the policy format.
For policies created after 2012-10-17, the version should typically be set to “2012-10-17”. It might seem small, but this detail can make a big difference in ensuring your policy is understood and implemented correctly.
ID
Feel free to add your own personal touch to your policies with the optional ID element! This feature allows you to easily keep track of and reference your policies within AWS. Of course, if you don’t require an ID, feel free to skip this step.
Statement
Defining permissions is a key aspect of the policy. It covers different access scenarios and can include multiple statements, each with its own set of properties.
Sid (Statement ID)
It’s actually an optional identifier that you can define yourself for a statement within a policy. It’s a great way to keep track of policies and document them, but it won’t alter the policy’s functionality in any way.
Effect
When it comes to granting or denying access, the “Effect” element is where it’s at. This element has two possible values that determine whether you’re in or out. It’s that simple!:
- “Allow“: Allows you to carry out the assigned tasks.
- “Deny“: Refuses to grant authorization for the assigned tasks.
Principal
When it comes to access to AWS resources, the “Principal” element is the star of the show. It’s the one that decides who gets in and who doesn’t.
And it has a lot of options to choose from – AWS services, IAM users, IAM roles, or even other AWS accounts. You can be specific about who you allow in or use a wildcard (*) to let anyone through.
AWS
When it comes to defining permissions for an AWS resource, you’ll need to specify which resource, service, or entity the policy applies to.
You can do this using the ARN (Amazon Resource Name) of the resource you want to define permissions for, whether it’s an S3 bucket or an AWS Lambda function.
Alternatively, you can use a wildcard (*) to indicate that you want to apply the policy to any resource. It’s all about getting the right level of access to the right resources!
Action
When you’re setting up access control for your AWS services, you’ll need to get familiar with the “Action” element. This element specifies the specific actions or operations that are allowed or denied.
Essentially, these actions are like requests you make to your AWS services. You can list out multiple actions for a statement or just use a wildcard (*) to represent all actions.
Resource
When it comes to defining AWS resources for actions, the “Resource” element is the key player. It’s all about that ARN, which is like a unique ID for each resource.
Whether you’re dealing with one resource or a whole list of them, this element has got you covered. So go ahead and get specific with your resources!
Example
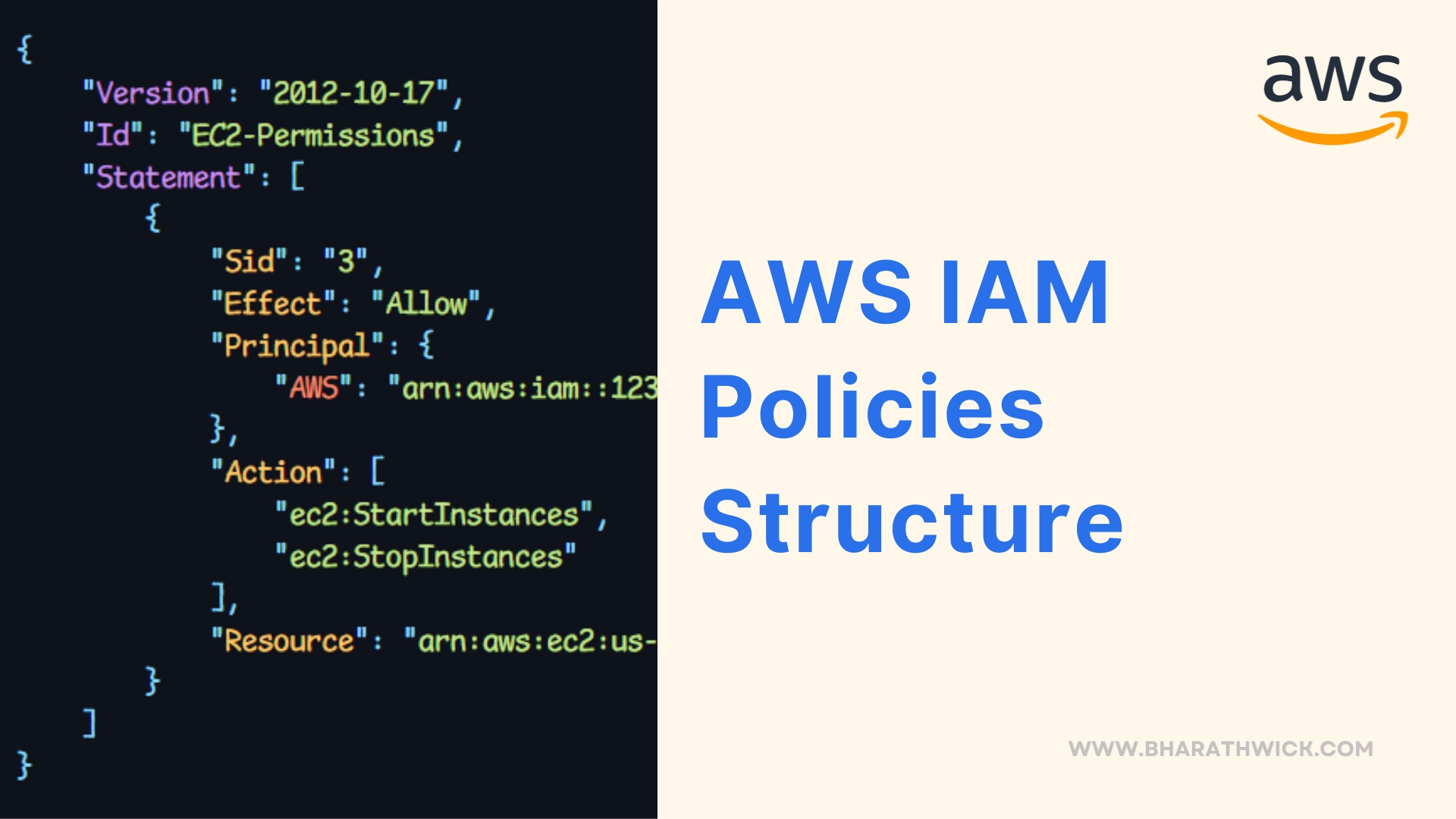
Check out this AWS IAM policy example that includes all the essential elements you need!
{
"Version": "2012-10-17",
"Id": "EC2-Permissions",
"Statement": [
{
"Sid": "3",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:root"
},
"Action": [
"ec2:StartInstances",
"ec2:StopInstances"
],
"Resource": "arn:aws:ec2:us-east-1:123456789012:instance/i-0123456789abcdef0"
}
]
}- Version: The policy uses the “2012-10-17” version of the policy language.
- Id: An optional identifier for the policy, set to “EC2-Permissions.”
- Statement: An array of statements, and in this example, there’s only one statement.
- Sid: An optional identifier for the statement, set to “3.”
- Effect: The statement allows (“Allow”) the specified actions.
- Principal: The policy applies to the AWS root user in account 123456789012.
- AWS: Specifies the AWS account or user to which the policy is applied.
- Action: This statement allows the “ec2:StartInstances” and “ec2:StopInstances” actions, which correspond to starting and stopping EC2 instances.
- Resource: The policy applies to a specific EC2 instance with the specified ARN (Amazon Resource Name).